Protecting Your Online Accounts
The first in a series of posts that provide simple tips that you can use to level up your own security.

As a professional in IT security, I am often approached by friends, family, and acquaintances who are looking for the best ways to avoid "being hacked".
This has inspired me to begin writing a series of posts that provide simple tips that you can use to level up your own security. Today I am going to focus on protecting your online accounts.
Why Online Accounts Get Hacked
Cybercrime is big business. In fact it has been estimated that it pulled in $1.5 trillion USD in 2018 - an amount that's approximately the size of Australia's GDP. The same report puts Data Trading at $160 billion USD of revenue, with much of this coming from the sale of your online accounts which could easily be worth $50 USD each.
Hackers can use your accounts for all sorts of nefarious activity including:
- Selling access to people who want a cheap Netflix, Spotify, Steam, or similar accounts.
- Posting scams/scams to your social media (cheap RayBans anyone?).
- Stealing money from your bank accounts, PayPal, or other online wallets.
- Stealing your identity.
- Using your email to take over your other accounts.
Spam postings may be a mild inconvenience, but having money or your identity stolen is no laughing matter. Despite the efforts of security team's around the world, these can be quite difficult to recover from, so managing and securing your own accounts is vital.
Protecting Vulnerable Accounts
Not all of our online accounts are equal, and it's acceptable to treat them with different levels of security. The following kinds of accounts are critical and definitely call for increased security measures:
Online Banking / Payment Websites. Pretty obvious, however this doesn't apply just to your online banking and PayPal, but also any other website that allows unfettered access to your money. As such you should also secure any accounts on any website with it's own payment system, share trading systems, or crypto currency exchanges.
Email Accounts. Email accounts are hacked every day, but there are many steps you can take to protect your sensitive material and personal information. This is crucial, because hackers can use your email as a gateway to many of your online accounts. Given that emails are usually the unique identifier for each of your online accounts, hackers can use this to manipulate their way in. The more savvy and skilled hackers will take it a step further covering their tracks, leaving you none the wiser until significant damage is already done.
Important Social Media. Your social media can be used to take over your identity, bringing real and serious problems once compromised. Not to mention, a hacker is also then in a position to attack the accounts of your friends and family, accessing personal information, photos and videos.
Government Accounts. Given the efficiency and ease of providing services online, government agencies often use websites to serve its citizens. It is important to protect these as the information they contain could easily be used to steal your identity or cause other serious issues for you.
This is by no means an exhaustive list of what needs to be done to protect your online accounts, however, it provides a solid start.
Why Protection Begins With Logging In
First, most websites rely on the login process to keep bad actors out. Once they're in your account, there tends to be a whole lot less detection and prevention systems in place. A worse case scenario is that a website will assume that because the login was successful, it must be a legitimate session. This gives the hacker free roam to do what they wish with your account. Even if the website does detect that something is amiss, it is often too late to undo the damage done. A good example would be having money stolen.
Second, as a user you have a lot of control over the process, such as picking the password and turning on features such as Two Factor Authentication. Your choices here can significantly improve the security of your accounts and the ability of the website operators to protect your accounts. As such, the actions you can take are going to be the focus of this article.
I've ordered each section from least to most effort required, however this also somewhat correlates to the level of protection provided and I strongly suggest you try to work through all sections.
Sign up for HaveIBeenPwned
Have I been Pwned is a service created by Australian Troy Hunt that tracks the information contained in leaked databases, allowing you to search for your own accounts and get notifications on new leaks.
Knowing about if you've been involved in a database leak is important as attackers will typically use these same leaked email addresses and passwords and attempt to use them on other websites. This is known as a credential stuffing attack and is effective due to most people reusing the same password across multiple websites. Approximately 60% of the population reuses passwords there's a good chance that you do - even I was guilty of this bad practice!.

Checking to see if your email address has been involved in any breaches is a smart move, and I also strongly suggest signing up to HaveIBeenPwned's notification service to alert you to breaches that may occur in the future.
Another valuable tool is the Pwned Passwords service which can tell you if a given password has been included in any known breach. Whilst a password being listed may not be a result of your account being leaked, being leaked does reduce the security of the account. This is because attackers will also use known breached passwords in more generic brute force attacks (where they will try common passwords against each account, rather than just the known pairings). I've looked into how Pwned Passwords protects passwords entered and trust it enough to use and recommend.
HaveIBeenPwned is in no way a silver bullet and there will be many leaks that have occurred but have not made their way into the hands of Troy to be added. So treat this service as backup insurance to solid password practices.
Turn on Two / Multi Factor Authentication
Companies like Google spend significant resources on improving their login systems to detect and block malicious attackers from logging into your account, however you can make this job significantly easier by using some form of two factor authentication whenever it is offered.
Two factor authentication (2FA) or multi-factor authentication (MFA) refers to using multiple factors in order for the website to determine you are who you say you are. You will already be familiar with the concept of a password, which is something that you know. Most websites will use rely on something that you physically have, such as access to a phone number (sms verification) or the phone itself (push notifications or a dedicated phone app).
Two factor authentication can protect you in situations where your username and password are known to the attacker, as it is unlikely that they will also have access to the second factor that is required. This is especially true of credential stuffing attacks, which are generally very simple and opportunistic in finding accounts without 2FA.
Whilst different forms of 2FA will have varying levels of security, especially when considering targeted attacks, any form of 2FA is better than nothing and can help prevent most automated attacks. Previously, I've relied on my own security assessments of 2FA methods (something which I hope to write about soon). However recently Google released research into the effectiveness of various methods including actual rates of prevention. I definitely recommend giving it a quick read.
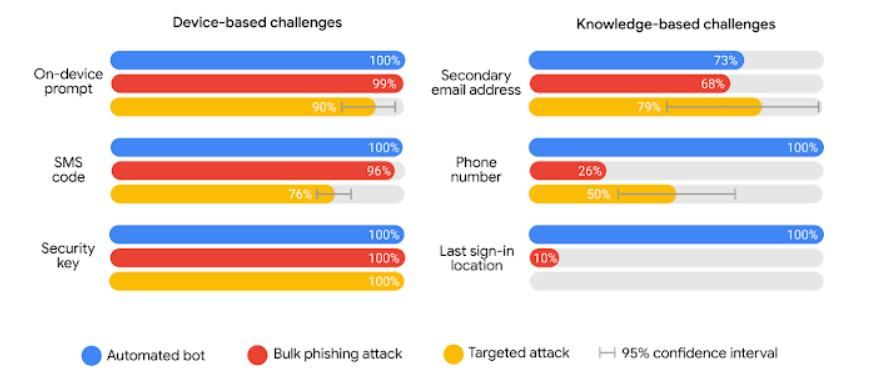
Turning on 2FA is an absolute must for your important accounts, and you may find that various websites or businesses already force some form of 2FA. You should look into what 2FA options are available, so you can find one that works for you in terms of both ease of use and level of security provided.
Using MFA can have downsides and it is important to be open about them. The biggest is that if you lose access to the thing that you have, you may also lose access to the websites that it was being used to protect. The most common scenarios to consider is using a phone number which you can't access whilst you are travelling overseas, or losing a phone that has your phone number or generated 2FA codes. While with some organisations, such as a bank, this can be fixed by visiting a branch, for purely web businesses such as Gmail this may be more problematic.
To avoid the lockout problem, many websites will let you back in by contacting support, answering questions, or setting multiple forms of MFA. However it is important to remember that in the case of a targeted attack, your security is only as good as the weakest link. That said, any form of 2FA is better than none.
Use a Password Manager
One of the common pieces of password advice you will hear today is to not re-use the same password across multiple accounts, and whilst this makes perfect sense given credential stuffing attacks from well known breached databases, its not that realistic.
I currently have about 100 personal accounts on different websites / services listed down. This easily doubles when taking into accounts I have for work. It's simply not realistic to have a strong unique password for each of them that I also remember.
Instead, I rely on a password manager - a piece of software that remembers my passwords for me. You may be thinking "how is this different to writing them down somewhere?" After all, this is basically what a password manager is – a digital list. Putting all your passwords in one place carries risks, because if it is stolen, a large number of accounts may be hacked (2FA may help though 😉). Therefore, your password list needs to be stored securely. This is where password managers come in - they are specialized pieces of software designed to keep your passwords secure.
Most password managers do this through the use of a "master password" which is used to protect all your passwords. This is generally done by using the master password to generate a key to encrypt all the other passwords with. This means you only need to memorize a master password, leaving your password manager to "remember" the rest. In fact, most password managers will generate strong passwords for you, so you don't even have to come up with a new one for each website.
In terms of what password manager to use, I personally use KeePassXC and Dashlane, whilst Troy Hunt uses and recommends 1Password. Of these, Dashlane and 1Password are online services which makes it super easy to have your passwords accessible from any device you use - including your phone. This ability to sync passwords across devices is the main reason I have Dashlane. On the other hand, KeePassXC stores your passwords on your local computer - you will need to sort out your own backups if you want them.
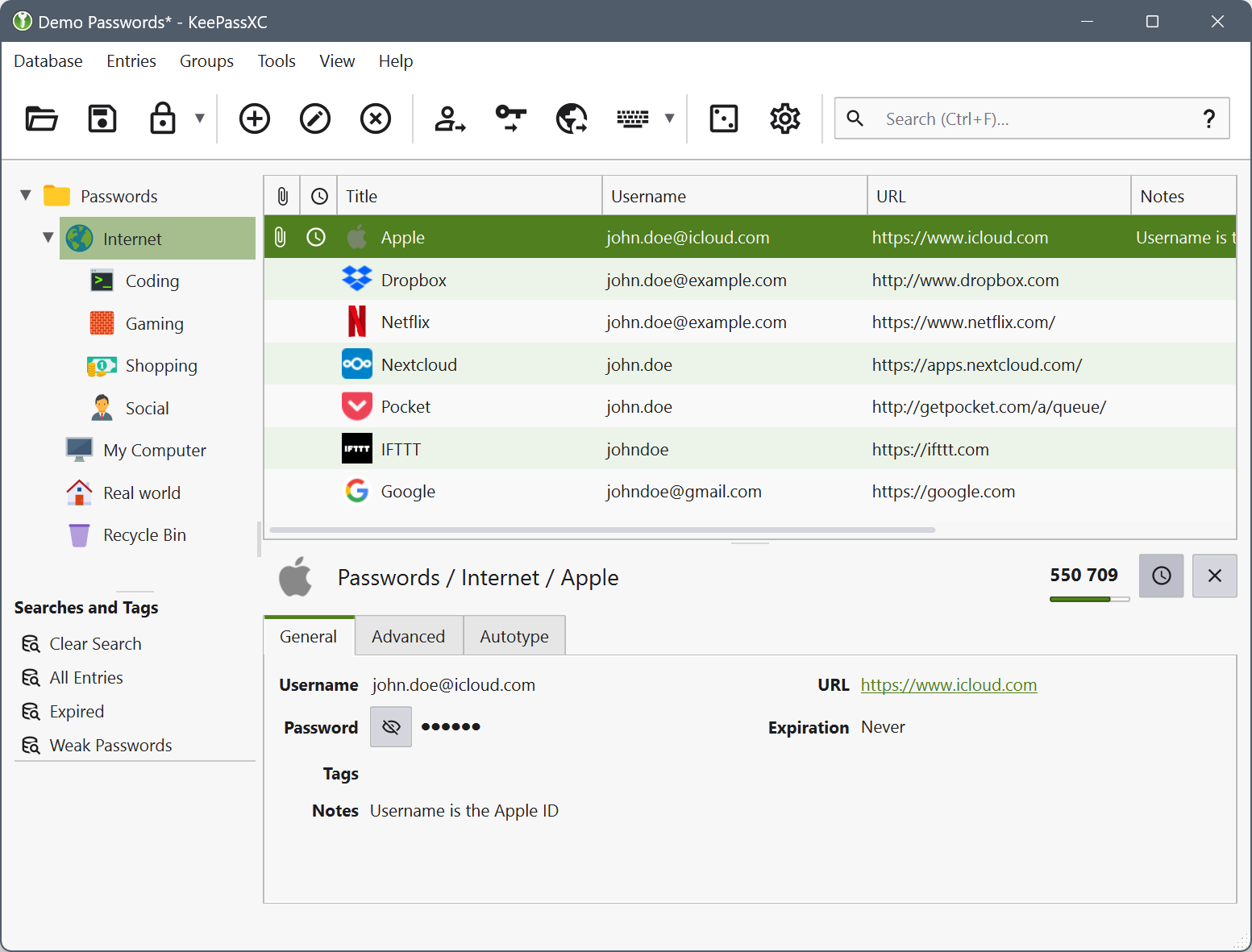
Password managers do have their drawbacks. As I mentioned earlier putting many or all of your passwords on one place it becomes a treasure trove for any hacker and as such I cannot stress the importance of securing your password manager. This is especially true of any online password managers that will be a target for hacking just like any other account.
Almost all your security will now rely on the strength of your master password. If you have a weak master password, the damage will quickly spread to all your other accounts. Luckily, thanks to your password manager you should only have to remember a small number of strong passwords - I personally have 3 memorised which are all used to get access to different password managers at home and at work. In picking a master password I tend to use a password manager to generate 16 character password with uppercase, lowercase, numbers, and symbols, until I have one that has a nice rhythm. The rhythm aids me in memorising it like you would memorise a phone number.
Finally, and most importantly, most password managers are designed in such a way that the only way in is with your master password. This is ideal from a security standpoint, but if you forget your master password, you lose access to all your other passwords. Although there are risks involved, sometimes writing it down and placing it somewhere safe until you are sure you've memorized it is necessary. I've certainly done this myself.
Password managers are designed in this way because while they provide a way to recover your account, it can also certainly be used for malicious purposes as well. By not providing such a backdoor, password managers have much higher security than they otherwise would.
Alternative - Use Delegated Login
Although it's possible to have a super strong password that not even you know thanks to your password manager, what if you could get rid of the password altogether? Many websites now let you login using your "socials" typically along the lines of your Google, Microsoft, Facebook, or LinkedIn accounts.
For example, Airbnb allows you to sign up/sign in using Google, Facebook, or creating your own account.
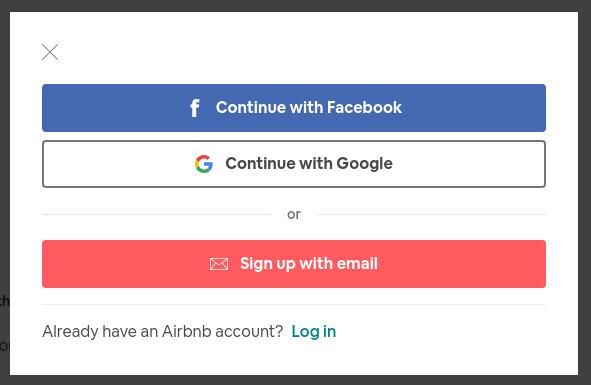
Using another service to login doesn't remove the need for good security practices, however, it can drastically reduce your attack surface. This means that you can focus your energy on having good security on fewer accounts, rather than sub-par security on many.